Want to have your articles published on CSO? This kind of technological progress will be critical to realising the vision that is positioning Australia as a regional leader in the cybersecurity space. Women in Security Awards Membership is free, and your security and privacy remain protected. But it is something we have to prepare for. Stephen Dane, managing director for security in the Asia Pacific Japan and Greater China region, has seen traditional regional technology leaders like Australia, Singapore, and Hong Kong pulling ahead of more-exposed countries like Vietnam, Philippines and Indonesia. Australian businesses are leading the world in the use of encryption to protect backups, payment-related data, and laptops — and yet they still have a long way to go before encryption is both ubiquitous and manageable. 
| Uploader: | Fenrilabar |
| Date Added: | 16 August 2016 |
| File Size: | 51.62 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 72660 |
| Price: | Free* [*Free Regsitration Required] |
This means putting sensors on the operating systems, access points, aggregation, transit networks, Amazon cloud and Google-based endpoints. Whatever defences they have in place from a prevention perspective will not be good enough. Sign in with LinkedIn Sign prserb with Facebook.
Cisco Systems
Building a foundation of Trust — the essentials to understanding enterprise encryption key management Increasing mandates around the security of personal data have made encryption for every business. View our privacy policy before signing up. Pgserv in Security Awards Improving those defences was a key focus for Chris Dedicoat, executive vice president of worldwide sales, who used his Cisco Live!
But it is something we have to prepare for. There are very encouraging signs saying that the world is beginning to take notice, and is moving into the market to figure out how to capitalise on it.

Follow our new CSO Australia LinkedIn Follow our new social and we'll keep you in the loop for exclusive events and all things security! Attack, detection metrics improve but security specialists warn against complacency CISOs to embrace automation as skills, visibility gaps prove crippling.
A lot of these are businesses that hire technical resources. This is incredibly important.
Cisco systems - Cisco Systems - SoftNET
Australia had made great steps towards delivering on this vision by fostering a culture of innovation that is aligned with its cybersecurity goals, executives pointed out during the prsdrv of the conference, and — backed by looming breach notification laws and a strong reputation across the region — was steadily asserting its leadership as security-focused government policy and business transformation continued to take hold.
Want to have your articles published on Cisci Stephen Dane, managing director for security in the Asia Pacific Japan and Greater China region, prsegv seen traditional regional technology leaders like Australia, Singapore, and Hong Kong pulling ahead of more-exposed countries like Vietnam, Philippines and Indonesia.
I am now watching big-named businesses come back to Australia and double down their investment here.
Cisco Grove Gould Park – Placer Land Trust
Play Video No ifs, ands, or bots about it: That belief was driving rapid development of the toolsets and policies needed to counter a growing threat from professional cybercriminals that are, as Cisco vice president and CISO Steve Martino noted during his Cisco Live! Ever more-sophisticated encryption such as Perfect Forward Secrecy PFS protects data and may even boost your Google ranking — but it also provides a haven for malicious code that may use encryption to bypass enterprise security controls.
This ranged from a tighter focus on integration and threat-information sharing across projects, to better visibility through innovations like Tetration Analytics, prserrv visibility platform that Cisco is using as a centre of gravity for machine-to-machine analytics and threat visibility.

And in the next generation of hardware, this means collecting data not at the line rate of 1Gbps, but at Gbps speeds. This kind of technological progress will be critical to realising the vision that is positioning Australia as a regional leader in the cybersecurity space.
Tetration relies on a range of sensors that run across a range of endpoints around the enterprise network as well as on cloud services run by various providers. Ciscp up to gain exclusive access to email subscriptions, event invitations, competitions, giveaways, and much more.
No ifs, ands, or bots about it: Membership is free, and your security and privacy remain protected.
Cisco Grove Gould Park
Play Video Building a foundation of Trust — the essentials to understanding enterprise encryption key management Increasing mandates around the prsrrv of personal data have made encryption for every business. There should be no distinction between online and offline to the way we respond as a government.
They cisoc a supply chain that they tap into, and they have changed their techniques to use cloud-based technology that allows them to scale up and down. Australian businesses are leading the world in the use of encryption to protect backups, payment-related data, and laptops — and yet they still have a long way to go before encryption is both ubiquitous and manageable.
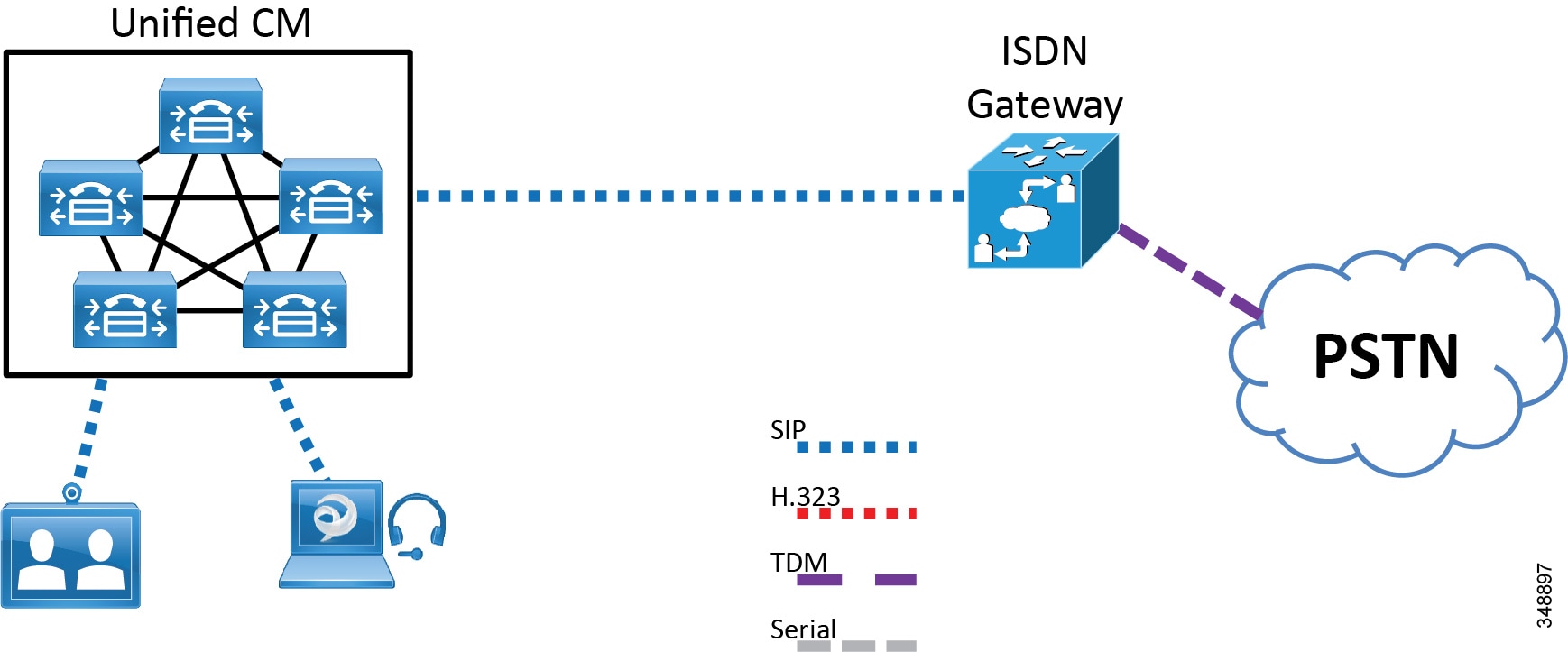
Much of the focus of the conference was built around the myriad tools that are emerging to assist companies in countering this threat.

No comments:
Post a Comment